
How To Build Centralized Authorization System
Learn what a centralized authorization system is and how you can implement it to streamline access control for your applications and services.

Learn what a centralized authorization system is and how you can implement it to streamline access control for your applications and services.
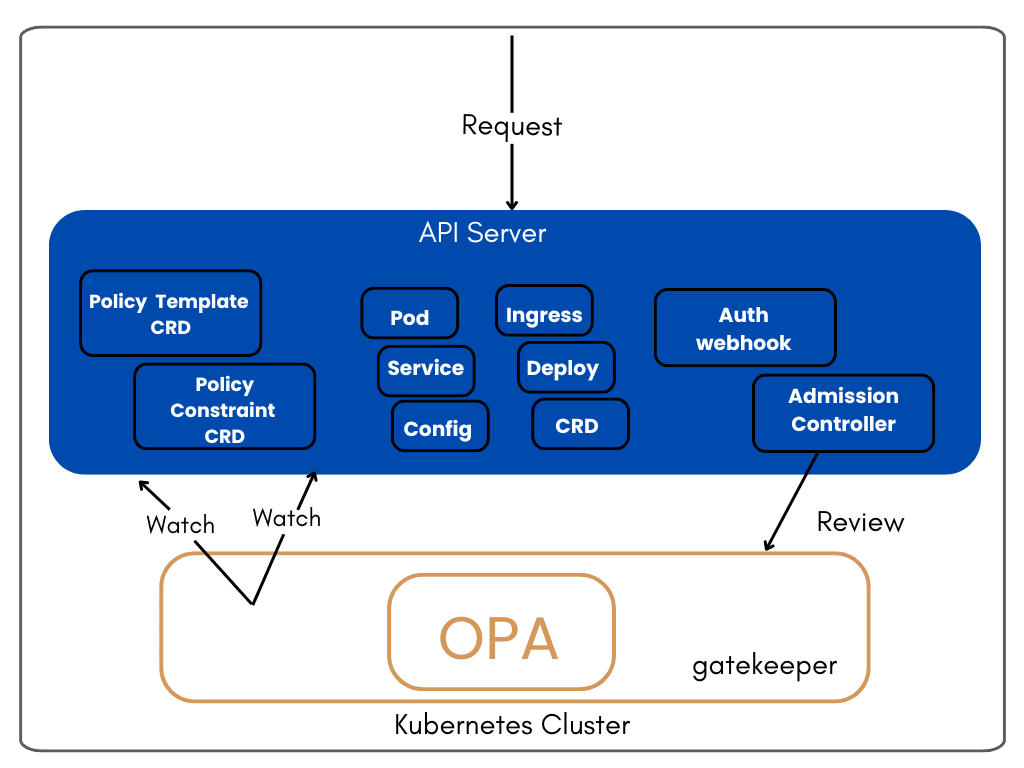
Learn how to leverage OPA Gatekeeper to write and enforce policies in Kubernetes clusters, ensuring security and efficient resource management in your environment.

In this article, you will learn top 6 open source authorization libraries ant their key factors that you should consider when choosing an authorization library.

In this post, you will learn about SAML and OAuth in detail. Additionally, you'll understand how each protocol works, their similarities and differences, and when to use one over the other.

In this tutorial, we will focus on implementing authentication using OAuth 2.0 in a Golang application.

In this article, we will explore identity and access management (IAM) and customer identity and access management (CIAM), examining how they differ, as well as their pros and cons.