
OAuth vs. JWT: Ultimate Comparison
Learn how to use OAuth and JWT to secure web applications. By reading this post, you will gain a clear understanding of when to use each one and how to implement them effectively in your apps.

Learn how to use OAuth and JWT to secure web applications. By reading this post, you will gain a clear understanding of when to use each one and how to implement them effectively in your apps.

This guide will walk you through the process of setting up role based authorization in your Next.js application using Permify, taking you from zero to a basic, functional implementation in mere minutes.
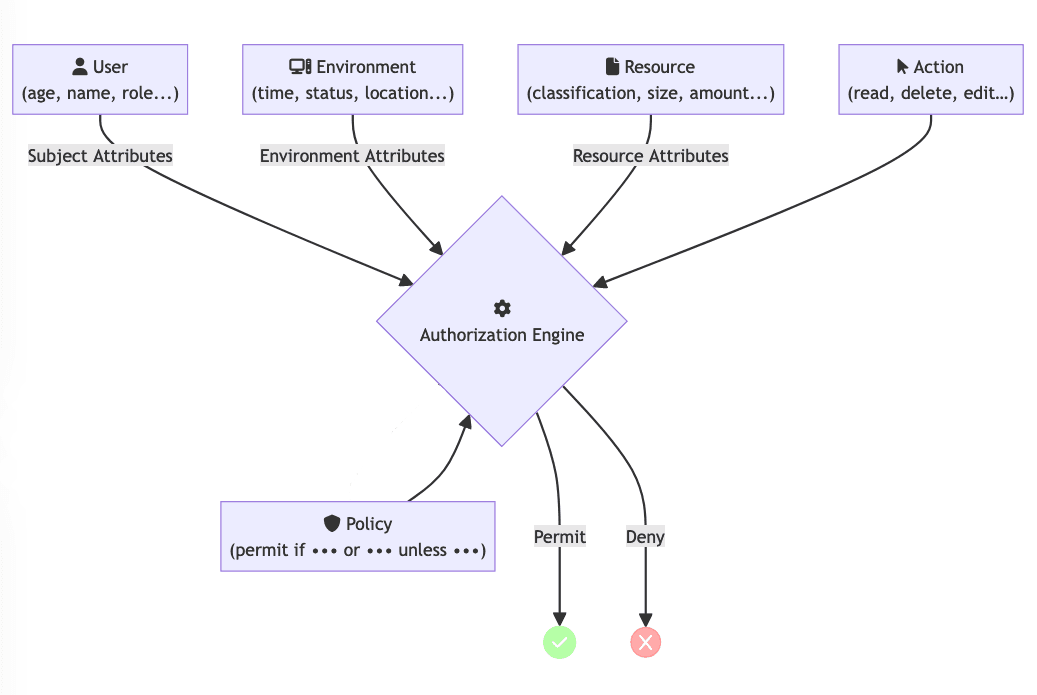
Learn everything you need to know about Attribute Based Access Control (ABAC) and develop an enterprise application to show the practical implementation of ABAC using Permify and Go.

In this piece, you will explore the 7 most popular open-source Keycloak alternatives that enterprises choose, and learn about the factors to consider when selecting an enterprise IAM solution provider.

Learn everything you need to know to implement Role-Based Access Control (RBAC) properly. Discover the basics, identify where it works best, find essential tools, and see how to overcome common challenges.

This post will provide you with a basic understanding of ACLs and give you a closer look at how Google uses them to build its consistent, global authorization system: Zanzibar.