 Next-Gen IGA
Next-Gen IGAAutomate Cloud Permissions Management with Just-In-Time Access
Gain complete visibility over access, automate access request and reviews, enforce least privilege with just in time provisioning — all from a single platform.
Automate Cloud Permissions Management with Least Privilege Access
Gain complete visibility over access, automate access request and reviews, enforce least privilege with just in time provisioning — all from a single platform.
78% of organizations experienced at least one
identity-related breach in the past year.
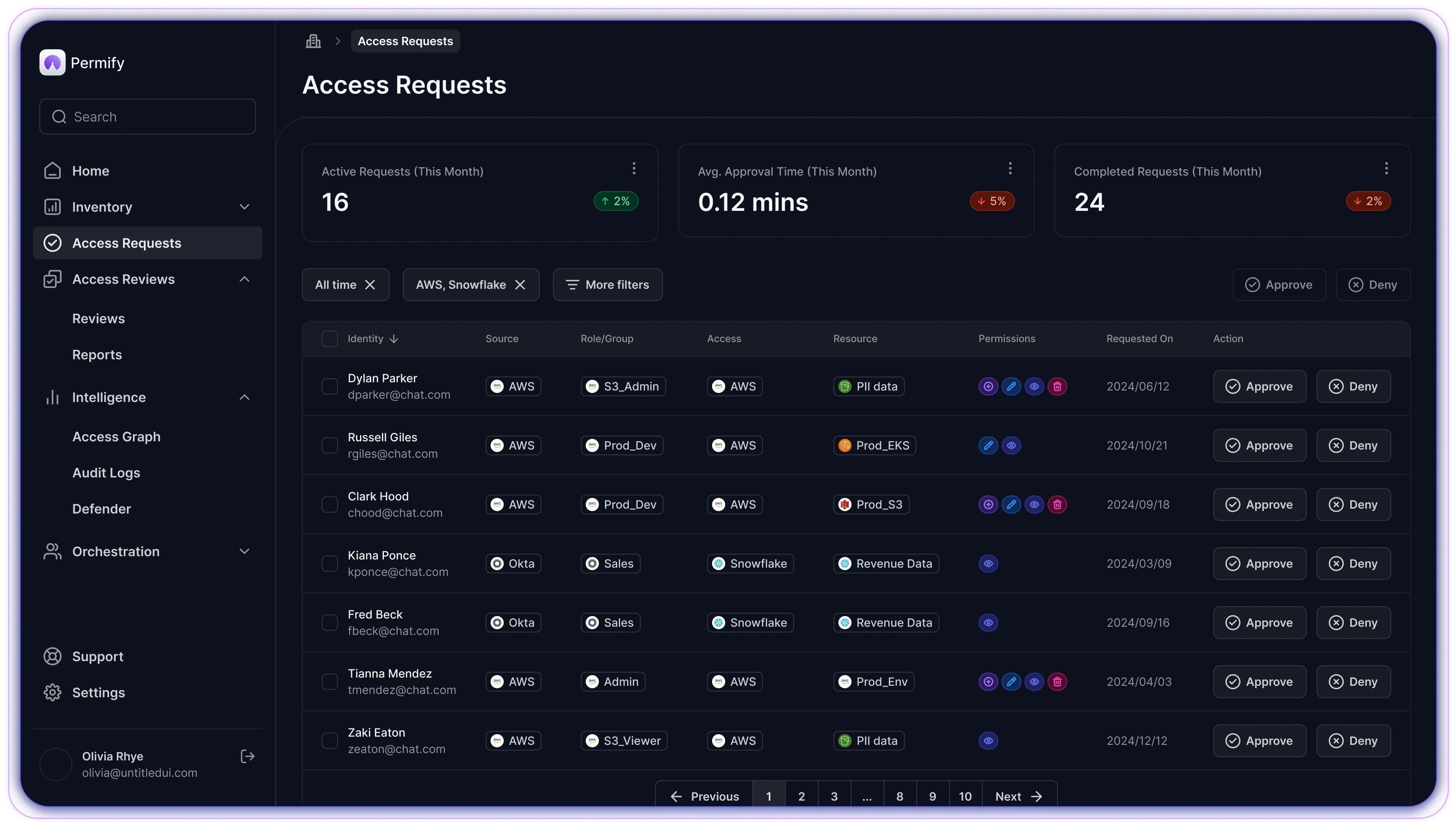
Centralized Access Provisioning
A single platform for granting and revoking access with customizable access levels
and time-limited permissions to give just-in-time and just-enough access.

“Permify enables us to implement fine-grained access controls in our system and centrally understand and govern the authorization. Permify team listens to feedback and acts on it quickly. Interacting directly with the designers and engineers of the service helps us strengthen our understanding of the concept and refine our usage of the product.”

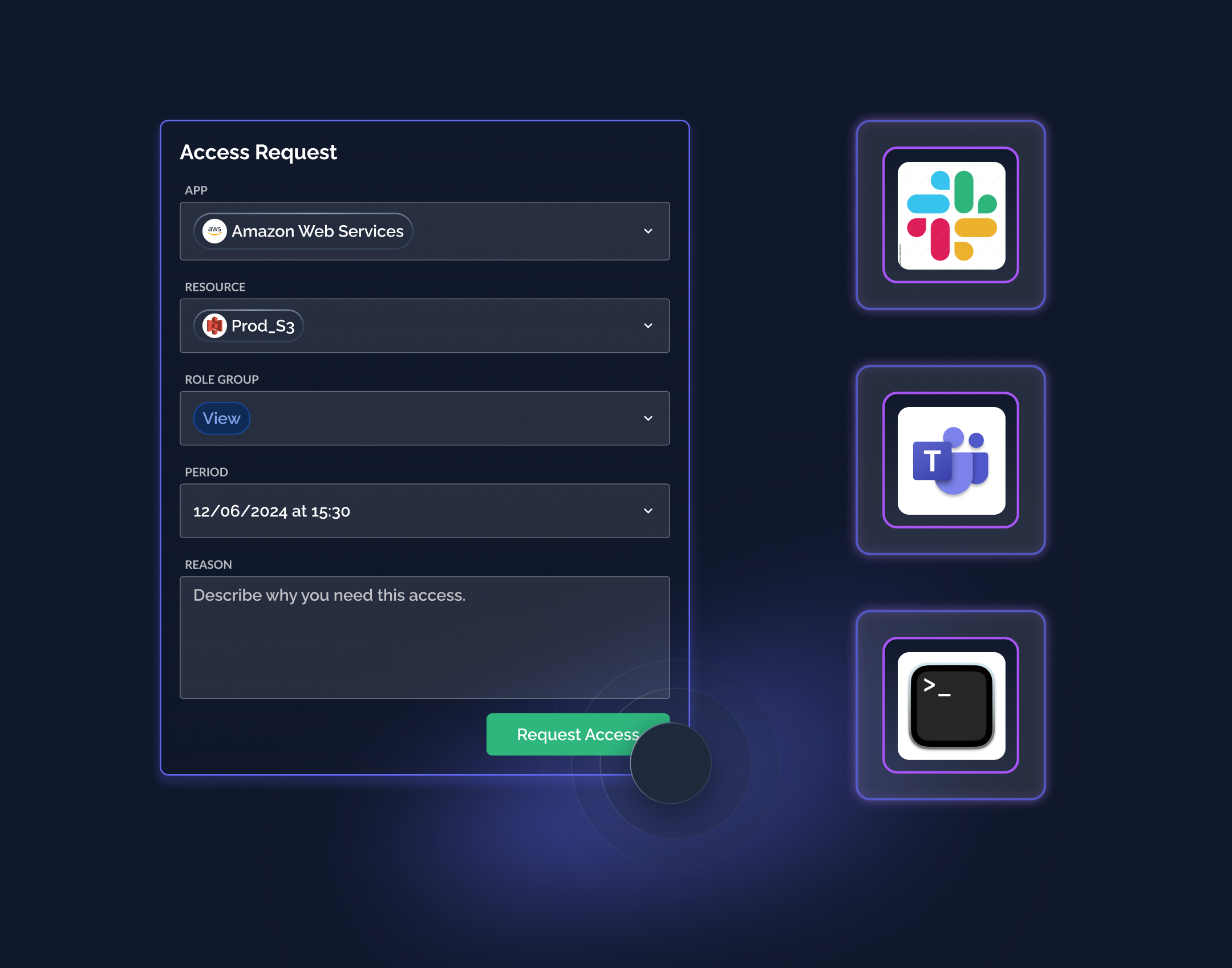
Self-Service Access Requests
Users can request access and approvers are notified seamlessly through Slack, MS Teams, Jira, or various other interfaces.
- Every access action is logged -
- detailing the individual who made the request, who approved it, and the reasoning and timing behind it helps streamline access evidence.
- No standing privileges -
- access requests can be time-bounded to reduce the risks of account takeovers, production errors, and insider abuse.
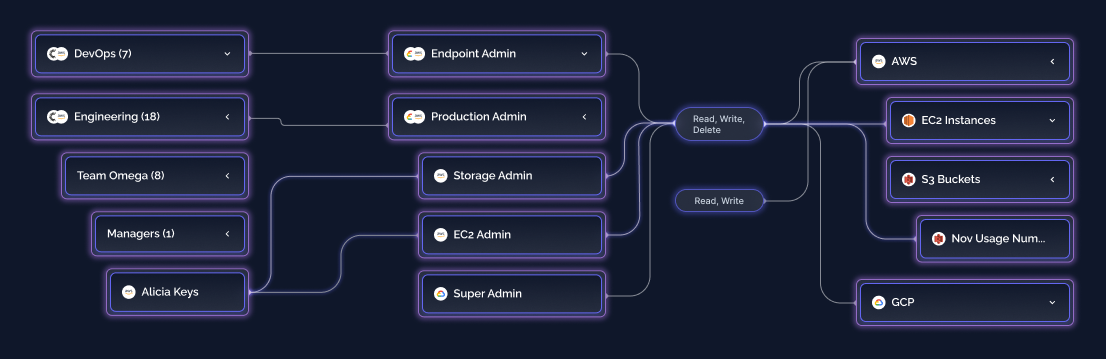
Eliminate the ambiguity of
who can access what and why
Pull all identity and access from native apps, infrastructure, and cloud resources, and map it into the Permify Access Graph. This enables real-time answers to the question:
"who has access to what and why?"

How It Works?
- Install the connector to connect your resources from tools you use such as AWS, GCP, Datadog, etc.
- Define who can request access to what with dynamic access workflow or policy in human readable language.
- Request access through your organizations preferred tool (Slack, Teams, etc.). It will be forwarded to the appropriate approvers.

