8 Best Identity and Access Management Tools in 2025
In this guide, we explore the top identity and access management (IAM) tools available today, comparing their features, strengths, and ideal use cases.

Digital identities are as crucial today as one’s physical identity, and because of this, Identity and Access Management (IAM) tools have become essential for businesses of all sizes. These tools help organizations control who is privy to what information, ensuring that only authorized individuals can access sensitive data and systems.
We’ll explore 8 of the best IAM tools currently available in the market, highlighting their top features and benefits. These tools cater to a range of use cases, from those focused on ease of use and scalability to more advanced options that support fine-grained access control, multi-factor authentication, and cloud-based integrations.
Without further ado, let's dive right in.
Factors to Consider When Choosing an Identity and Access Management (IAM) Tool
When choosing an IAM tool, you first need to carefully consider the following factors to ensure it satisfies your short-term and long-term needs. To do this, you have to ask the following questions:
#1: Is It Scalable and Flexible?
A good IAM tool should be scalable and flexible to accommodate the growth and evolving needs of your organization. As your business expands, it should effortlessly support and handle more users, devices, and applications.
The last thing you want is a system that works well for a small team but struggles as your business grows.
The tool should also easily integrate with a wide range of software and systems, whether on-premises, cloud-based, or hybrid. This adaptability prevents the need for frequent replacements or overhauls of your IAM system, saving time, effort, and resources in the long run.
#2: Is It Secure and Legal-Compliant?
Security is non-negotiable for any IAM tool because it controls access to your organization’s sensitive data. You need to look for a tool that offers features like multi-factor authentication, single sign-on, and role-based access control, as these features help keep your data safe from unauthorized users.
Compliance is equally important. Ensure you get acquainted with the specific regulations governing your industry and select a tool that meets these regulatory standards to protect your organization from legal issues.
#3: Is It Easy for Your Whole Team To Use the Tool?
Even the most secure and flexible IAM tool needs to be user-friendly. A steep learning curve will discourage your team members from using it correctly or consistently, leading to security gaps and inefficiencies in managing access controls.
Opt for an intuitive and easy-to-use tool to prevent these issues and foster better team collaboration.
What Are the Best Identity and Access Management Tools?
-
Okta — Cloud-based IAM solution featuring single sign-on and passwordless authentication for seamless user access.
-
FusionAuth — Developer-centric IAM and CIAM, customizable authentication flows, and scalable features designed for modern applications and fast-growing businesses.
-
CyberArk — Security-first solution specializing in privileged access management (PAM) to safeguard critical systems and sensitive data.
-
ForgeRock — IAM platform delivering robust identity management, access management, and governance for enterprise environments.
-
OneLogin — Cloud-based solution with single sign-on and multi-factor authentication for secure application and data access.
-
SailPoint — Comprehensive solution emphasizing identity governance, risk management, and compliance through enhanced visibility and control.
-
EmpowerID — Customizable IAM and cloud security platform for managing identities, roles, and access across both on-premises and cloud systems.
-
Zluri — All-in-one SaaS management platform integrating IAM capabilities to optimize application usage, access controls, and compliance for SaaS tools.
#1: Okta
Best for: Securing user access to applications and data
Similar to: OneLogin, CyberArk

Okta's Workforce Identity Cloud is a comprehensive IAM solution designed to provide secure access for employees, contractors, and business partners from any device, anytime, and anywhere. It enhances security and user experience while enabling organizations to streamline their IT operations.
Who Is It For?
Okta’s solution is built for everyone within an organization, from individual employees to IT teams and business partners.
Okta’s Top Features

-
Okta provides secure cloud-based single sign-on (SSO), allowing users to access multiple applications with one set of credentials.
-
Okta enables passwordless authentication and offers intelligent, secure access that adapts to user behavior and context, enhancing security without sacrificing user experience.
-
Okta manages user access rights to ensure that individuals have the appropriate permissions for their roles.
Okta Pricing
Okta offers a free trial of their Workforce Identity Cloud that potential customers can take advantage of to evaluate the platform's features and capabilities before committing to a paid subscription. They also offer various price points based on the number of users and the specific features an organization requires.
This means that the pricing varies depending on the combination of features you need. You can contact Okta’s sales for more information and to get started.

Okta Pros and Cons
-
Okta provides a unified platform for managing user identities, including SSO, MFA, lifecycle management, and more.
-
Okta enables secure access to applications and resources from any location, making it suitable for dynamic work environments.
-
It offers no-code automation for identity processes, allowing IT teams to focus on strategic operational initiatives.
-
It has a complex pricing model.
-
Customization options for Okta are often restricted without higher-tier plans.
#2: FusionAuth
Best for: Modern businesses looking for developer-friendly, flexible, and scalable identity management.
Similar to: Auth0, Okta
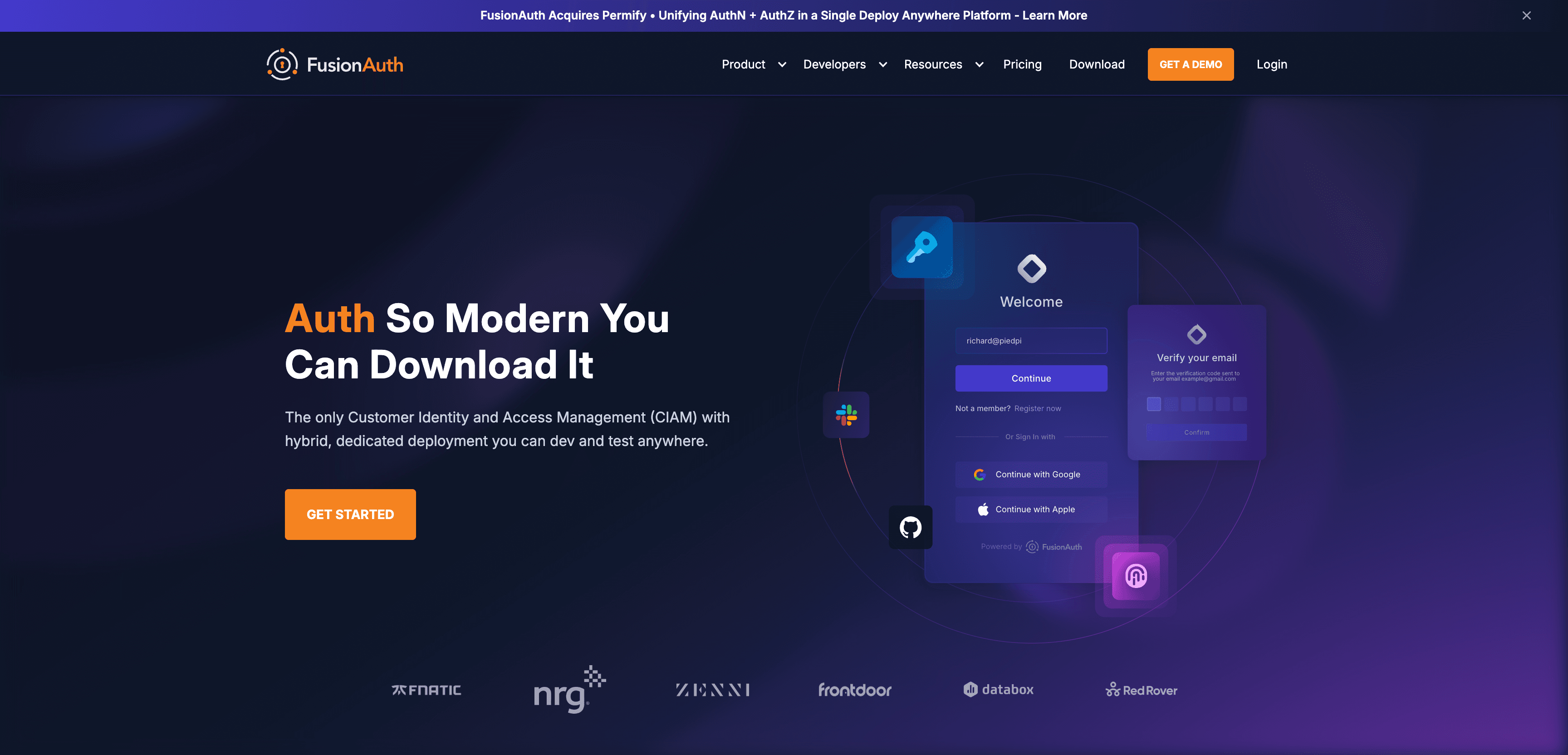
Founded in 2018, FusionAuth is a full-featured identity and access management (IAM) platform built specifically for developers who need complete control over authentication, authorization, and user management. Known for its flexibility, developer-first design, and on-premise/cloud deployment options, FusionAuth supports fast integrations for startups while also scaling to meet enterprise-grade compliance and performance requirements.
FusionAuth provides a modern approach to IAM with customizable flows, built-in CIAM capabilities, and a pricing structure that remains predictable as you scale.
Who Is It For?
FusionAuth is ideal for startups, growing SaaS companies, and enterprises that need a customizable, developer-friendly IAM solution. It’s especially useful for teams that want:
- Self-hosting or private cloud options
- Flexible APIs
- Advanced CIAM features without vendor lock-in
- Predictable pricing
FusionAuth’s Top Features
-
FusionAuth delivers a unified authentication experience across all applications, supporting OAuth, OIDC, and SAML out of the box.
-
It includes highly customizable login flows, themes, and user journeys—allowing businesses to create tailored experiences without compromising security.
-
FusionAuth also provides powerful user and tenant management, MFA support, passwordless login, OAuth workflows, and a robust API surface for developers.
-
Additionally, FusionAuth offers built-in registration flows, email templates, security policies, and advanced user consent management.
-
Its event-driven architecture and webhooks enable seamless integration with existing systems, making it easy to embed IAM into any stack.
FusionAuth Pricing
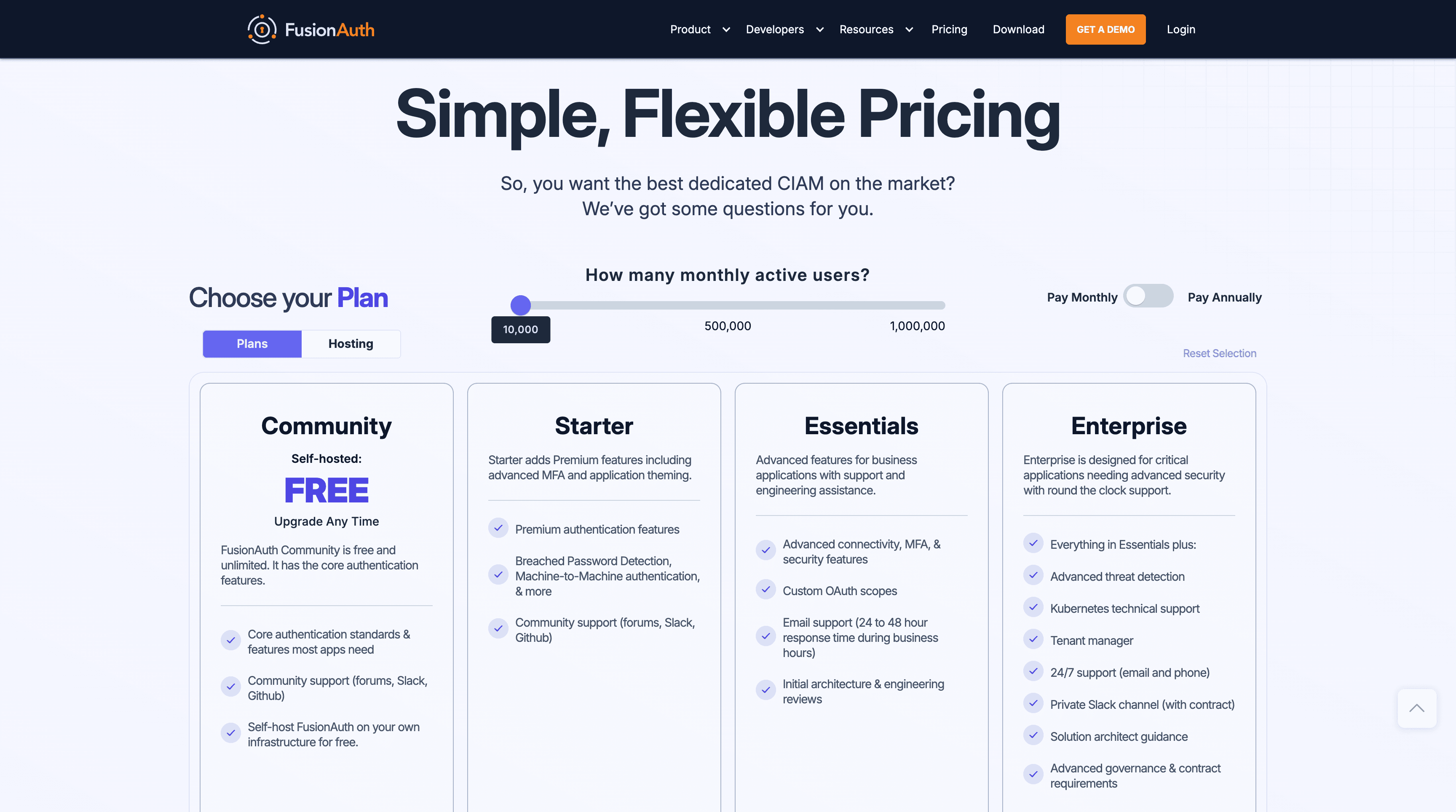
FusionAuth provides a free community edition, making it an attractive option for startups. Paid plans scale based on usage and features, covering cloud hosting, advanced support, and enterprise add-ons. Pricing remains transparent and predictable, and businesses can choose between self-hosted or cloud deployments depending on security needs.
FusionAuth Pros and Cons
-
Extremely developer-friendly, with complete API coverage and SDKs
-
Flexible deployment: on-premise, private cloud, or FusionAuth Cloud
-
Strong passwordless, passkey and MFA support
-
Transparent, predictable pricing with a usable free plan
-
Supports modern standards like OAuth2, OIDC, SAML, and WebAuthn
-
Easy integration with modern apps, microservices, and legacy systems
-
UI customization is flexible but requires developer effort
-
Some advanced features (e.g., SCIM, advanced threat detection) are locked behind higher tiers
#3: CyberArk
Best for: Established enterprises with legacy systems and stringent compliance demands.
Similar to: Okta, Zluri

Founded in 1999, CyberArk is a leader in privileged access management (PAM) that secures access to critical assets and meets compliance requirements by managing and monitoring privileged accounts and access across an organization's IT environment.
CyberArk offers broad compliance features and a more extensive enterprise-oriented service, focusing on complex deployments and high scalability.
Who Is It For?
CyberArk is ideally suited for large enterprises that need to secure sensitive information and manage access to critical systems and data.
CyberArk’s Top Features

-
With CyberArk, users can securely access multiple applications with a single set of credentials, improving security and user experience.
-
CyberArk securely stores and manages credentials in a centralized repository, automating password rotation and enforcing policy compliance.
-
It also provides the ability to monitor, record, and audit all privileged sessions, offering real-time visibility and playback capabilities to enhance security and compliance.
CyberArk Pricing
While CyberArk offers a free 30-day trial, it doesn't explicitly state the exact cost of its services. Instead, CyberArk encourages prospective customers to contact sales for a customized quote.
CyberArk Pros and Cons
-
It offers detailed reporting and auditing capabilities that help organizations meet stringent compliance standards, such as GDPR, SOX, and HIPAA.
-
Uses advanced analytics and machine learning to detect and respond to internal and external threats in real time.
-
Boasts a wide range of integration with On-premise and Cloud-based data centers.
-
While great for enterprises, CyberArk is one of the most expensive PAM solutions available, with the additional costs of professional services and management post-deployment.
-
Many users report that CyberArk can be complex to deploy and manage, requiring significant expertise and resources, which might be challenging for smaller IT teams.
#4: ForgeRock
Best for: Organizations with complex, large-scale, and diverse identity requirements.
Similar to: Okta, Zluri

ForgeRock (merged with PingIdentity) is a comprehensive digital identity platform that manages, secures, and orchestrates user identities and interactions across devices, applications, and services. It specializes in consumer identity and access management (CIAM), offering tools for identity governance, access management, and directory services.
Who Is It For?
ForgeRock is designed for large enterprises and organizations that require robust, scalable solutions for managing consumer identities across multiple platforms.
ForgeRock’s Top Features
-
ForgeRock Access Management provides secure authentication, authorization, and single sign-on capabilities to protect access to applications and resources.
-
ForgeRock Identity Management enables organizations to manage the complete identity lifecycle, including user provisioning, self-service, and identity governance.
-
It automatically adjusts user access rights based on real-time changes in roles or attributes, improving security and compliance.
ForgeRock Pricing
-
Free trial: ForgeRock provides a free trial that allows full access to platform modules, enabling potential customers to evaluate the services before committing to a purchase.
-
User pricing: This depends on the specific services and volume of users.
-
Implementation cost: For a global enterprise, the initial implementation cost is approximately $20,000, with ongoing costs estimated at around $8,000 per month
It’s best to contact the sales team to get a proper pricing structure that fits your business needs and budget.
ForgeRock Pros and Cons
-
It is flexible enough to handle large-scale deployments effectively, making it suitable for organizations that anticipate growth or have a high volume of transactions.
-
ForgeRock provides tools to create unique and secure user experiences, enhancing customer satisfaction and loyalty.
-
ForgeRock offers a solid IAM system encompassing various functionalities, including user management, access control, and identity governance.
-
ForgeRock's pricing can be high, especially for smaller organizations or startups. The need for customized solutions may also lead to additional costs that can add up over time.
-
Organizations may experience challenges if they decide to switch IAM providers after implementing ForgeRock, as migrating data and processes can be complex and resource-intensive.
#5: OneLogin
Best for: Organizations that require robust identity and access management solutions.
Similar to: Okta, CyberArk

OneLogin is a cloud-based IAM solution that secures employee, customer, and partner data. It has over 6,000 direct integrations with several applications, including on-premises applications. With OneLogin, businesses can manage user identities, control system access, and ensure security across multiple devices.
Who Is It For?
OneLogin is suitable organizations of all sizes that need to manage and secure user access to applications and data across their IT environment.
OneLogin’s Top Features

-
Single Sign-On (SSO) functionality, which enables users to to log in once and gain access to multiple applications without needing to re-enter credentials. This offers a pleasant user experience and reduces reduces password fatigue, as users can access 6,000+ pre-integrated applications through a single portal.
-
Extra security with OneLogin’s Multi-Factor Authentication (MFA) feature, requiring users to provide additional verification methods beyond just a password.
-
OneLogin automates the management of user identities throughout their lifecycle, from onboarding to offboarding.
OneLogin Pricing
OneLogin's pricing structure provides flexibility and value to customers, offering both individual feature price costs and bundled services.
-
Advanced Bundle: Includes SSO, advanced directory, and MFA for $4.00 per user/month (a savings compared to purchasing separately for $6.00).
-
Professional Bundle: Includes all advanced bundle products, identity lifecycle management, and HR-driven identity for $8.00 per user/month (compared to $12.00 if purchased separately).

OneLogin Pros and Cons
-
A one-stop solution for users having all necessary software tools like email, HR portal, and CRM.
-
The tool specializes in managing consumer identities with tools for registration, authentication, and user profile management.
-
OneLogin is highly flexible and user-friendly for both administrators and end-users to navigate.
-
Some users have experienced slow connectivity, leading to delays in accessing necessary applications.
-
While the basic interface is user-friendly, organizations without dedicated IT teams will struggle to master OneLogin's advanced features.
#6: SailPoint
Best for: Security-conscious enterprises, particularly those in highly regulated industries or with significant remote workforces.
Similar to: ForgeRock, Okta, OneLogin

SailPoint enables modern enterprises to efficiently manage and secure access to their data, software, and applications through a unified, centralized dashboard. It focuses on enhancing security and compliance through automated access certifications, policy management, and role-based access control.
Who Is It For?
Organizations seeking to strengthen their security posture through rigorous identity governance and access management, especially useful in industries such as finance, healthcare, and government.
SailPoint’s Top Features

-
SailPoint provides robust identity governance capabilities for managing user identities, access privileges, and entitlements, ensuring that only authorized users have access to sensitive data.
-
Users can request access to applications and resources, with automated approval processes based on predefined policies and workflows.
-
SailPoint implements Single Sign-On (SSO) to allow users access multiple applications with a single set of credentials, further enhancing user experience and security.
SailPoint Pricing
SailPoint offers three different product tiers: Standard, Business, and Business Plus, but you’ll have to contact its sales team for precise cost information.

SailPoint Pros and Cons
-
The centralized access monitoring reduces the risk of unauthorized user access and data breaches.
-
As your organization grows, SailPoint's architecture is designed to accomodate and scale alongside.
-
It offers audit trails and reporting features that facilitate compliance efforts.
-
Comapred to other IAM tools, some users have reported SailPoint’s interface lacks intuitiveness.
-
SailPoint solutions are often seen as expensive due to software licensing fees, infrastructure costs, and ongoing maintenance, making them less accessible for smaller organizations.
#7: EmpowerID
Best for: Large organizations with complex IT environments.
Similar to: Okta, OneLogin
 EmpowerID offers a versatile IAM solution that excels in identity governance and administration (IGA), providing fine-grained access controls and comprehensive lifecycle management. It operates under a Zero Trust model, emphasising security through strict access controls and continuous verification of user identities.
EmpowerID offers a versatile IAM solution that excels in identity governance and administration (IGA), providing fine-grained access controls and comprehensive lifecycle management. It operates under a Zero Trust model, emphasising security through strict access controls and continuous verification of user identities.
Who Is It For?
Medium to large organizations looking for a comprehensive identity and access management solution that supports a hybrid environment with both on-premises and cloud resources.
EmpowerID’s Top Features
-
It offers single sign-on (SSO) feature and multi-factor authentication (MFA) methods, simplifying and adding an axtra layer of security to the log-in process.
-
EmpowerID allows users to change or reset their passwords through a self-service password management platform.
-
It automates the management of user identities throughout their lifecycle, ensuring that access rights are appropriately assigned and revoked as needed.
EmpowerID Pricing
EmpowerID uses 3 pricing models; per person, per admin, and per server. It also uses 3 additional pricing modules grouped as follows:
-
Per Person Licensing Modules
-
Not Per Person Licensing Modules
-
Advanced Modules (all advanced modules are currently licensed on a per person basis)
Like Okta, the overall pricing depends on thefeatures you need, as each feature has an individual price depending on the pricing model you choose.

EmpowerID Pros and Cons
-
The platform is highly customizable, allowing you to tailor the identity management processes to your needs and compliance requirements.
-
The Zero Trust approach verifies all access requests, no matter where they come from.
-
Provides a visual identity modeling tool that simplifies the management of identities and access, making it accessible for users with varying technical expertise.
-
While offering robust features, the cost can be high, especially for smaller organizations or those with less complex needs, potentially impacting ROI.
-
While EmpowerID offers mobile applications for MFA, its mobile support is still a drag.
#8: Zluri
Best for: Modern enterprises that need unparalleled visibility and control across their software-as-a-service (SaaS) applications, access and cost.
Similar to: Okta
 Zluri is a comprehensive SaaS management platform designed to help organizations manage and optimize their software as a service (SaaS) applications. It focuses on streamlining SaaS operations, enhancing security, and improving cost efficiency through centralized monitoring and management of all SaaS subscriptions.
Zluri is a comprehensive SaaS management platform designed to help organizations manage and optimize their software as a service (SaaS) applications. It focuses on streamlining SaaS operations, enhancing security, and improving cost efficiency through centralized monitoring and management of all SaaS subscriptions.
Who Is It For?
Zluri is designed for companies looking to gain better visibility and control over their sprawling SaaS ecosystems, ensuring compliance, reducing redundant subscriptions, and managing software spend effectively.
Zluri’s Top Features

-
Zluri automatically discovers all SaaS applications in use, providing a comprehensive inventory and visibility into SaaS spend and utilization.
-
It helps manage and optimize SaaS licenses, preventing overspending on underutilized or redundant software subscriptions.
-
Zluri supports custom integrations through open APIs, enabling organizations to consolidate multiple app instances and streamline operations without relying on third-party tools.
Zluri Pricing
Zluri does not explicitly state the exact cost of its services. However, it offers tailor made pricing plans based on the features and scale of the service your organization requires.
Zluri Pros and Cons
-
Zluri gives users robust security monitoring and compliance tracking to ensure SaaS applications adhere to internal policies and external regulations.
-
With its automation tools, Zluri streamlines operational processes, reducing manual effort and minimizing human error.
-
Zluri’s centralized management dashboard improves efficiency and makes it easier for IT teams to maintain control over software usage.
-
While Zluri offers extensive integration options, setting up and maintaining integrations with all SaaS applications can be cumbersome and time-consuming for IT teams.
Elevate Your Security Measures with Identity and Access Management Tools
Choosing the right Identity and Access Management (IAM) tool is crucial for ensuring the security, compliance, and efficiency of an organization's IT environment. As we've explored, there are a variety of IAM tools available, each with its unique strengths and capabilities suited for different organizational needs and scales.
All the tools on our list each offer unique strengths, from cloud-based solutions like Okta, FusionAuth and OneLogin that offer seamless single sign-on and multi-factor authentication, to more specialized platforms like CyberArk for privileged access management, and comprehensive SaaS management solutions like Zluri, the options are extensive.
By carefully evaluating each tool's features, pricing, and suitability for your specific use case, you can make an informed decision that will safeguard your digital assets and streamline access management processes.
Ultimately, the right IAM tool will enhance your organization’s security posture, support compliance efforts, and improve overall operational efficiency, contributing to a stronger, more resilient IT infrastructure.
