Scalable Authorization Without Data Management Hassle
Set up fine-grained authorization with a centralized service approach inspired by Zanzibar with streamlined data synchronization and management functionality.
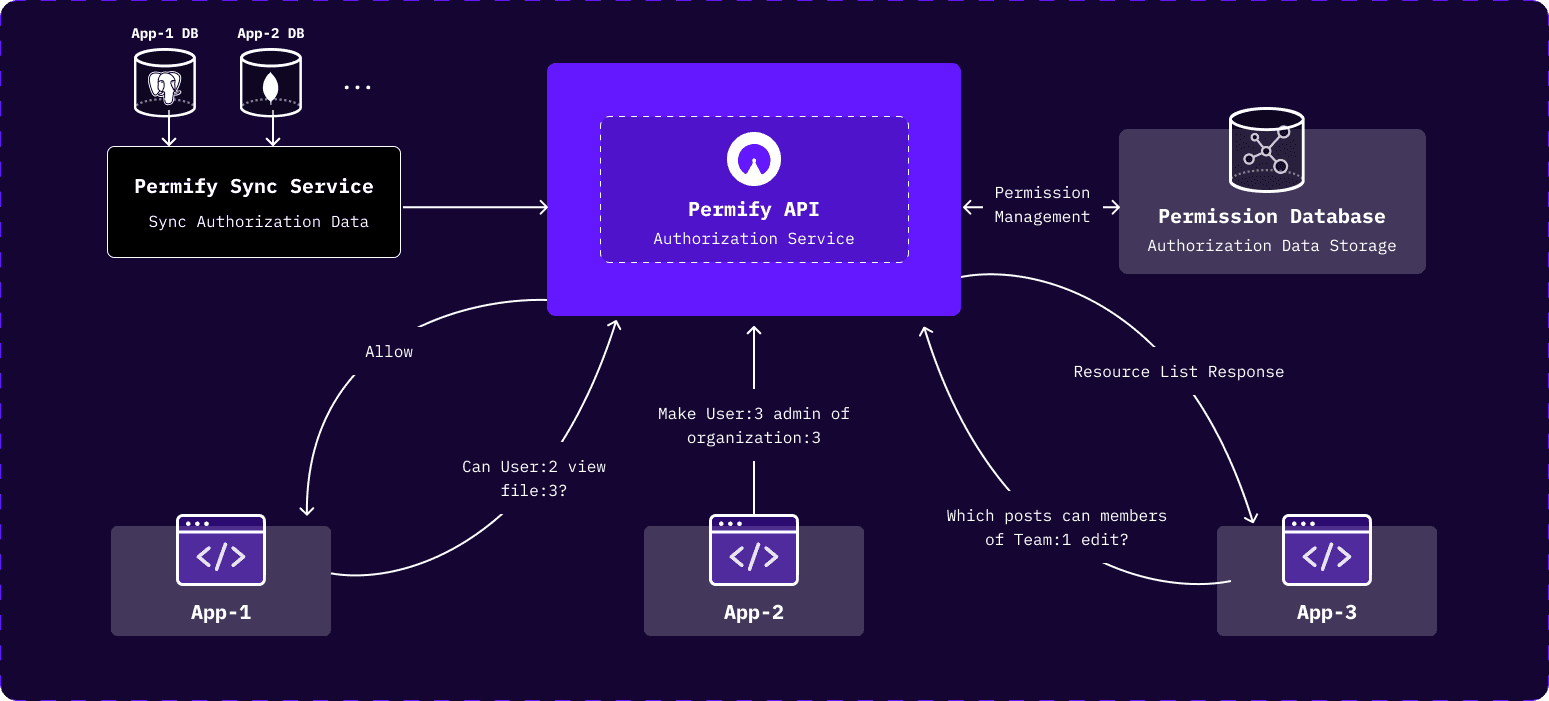
Sync Authorization Data in Real Time, Without Dealing with API Requests
Efficiently handle updates to permissions and roles without manual intervention or dealing with API requests. Permify Sync Service automatically captures changes in your application's database and syncs authorization-related data with Permify in real time.
Streamlined Policy Management
Unlike OpenFGA, we're taking an approach that help engineering teams to ease and streamline the management and collaboration of their authorization logic.
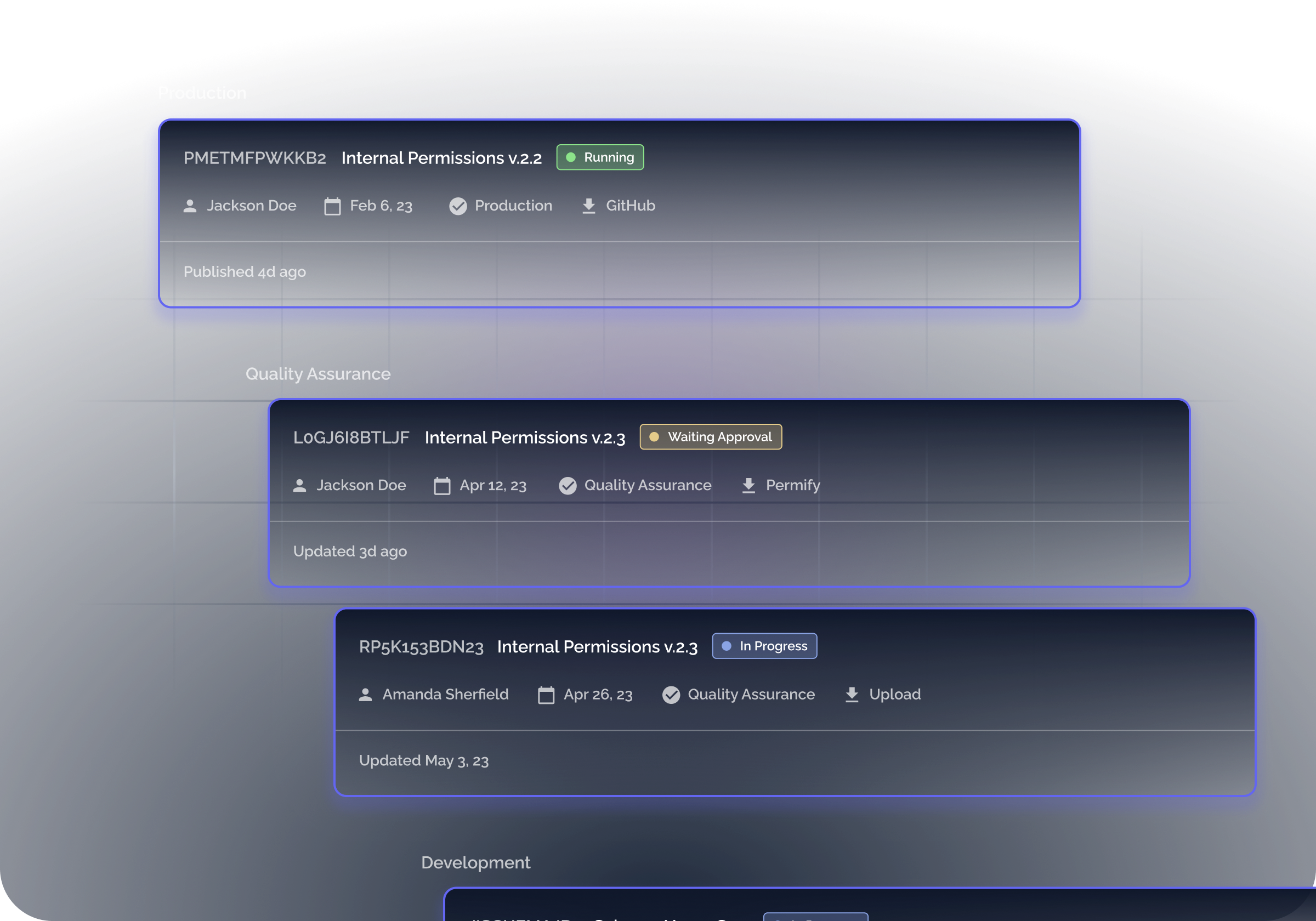
Schema Staging with GitOps Workflow
Handle schema changes in different stages and deploy schemas with our GitOps workflow, specifically designed to approve/merge and monitor schema changes.
Partial Schema Update
Make partial updates to your policy by adding or modifying actions within individual entities without need to change the whole policy.


Permify enables us to implement fine-grained access controls in our system and centrally understand and govern the authorization. Permify team listens to feedback and acts on it quickly. Interacting directly with the designers and engineers of the service helps us strengthen our understanding of the concept and refine our usage of the product.


Permify has empowered our team at Dynamic Yield to implement precise access control and streamline our authorization processes. The team at Permify is incredibly responsive, taking our feedback seriously and helping us maximize the platform's potential. Their support and direct interaction have greatly enhanced our understanding and use of the product.

Global Available Securely Managed
Global Clusters
Choose from your preferred region supported by AWS, GCP, or Azure to set up and deploy your authorization system in minutes.
Private Link
Ensure exclusive access to your authorization systems to trusted networks only, removing whole categories of security vulnerabilities.
Disaster Recovery Zones
Strategically located zones replicate data across regions, ensuring rapid recovery and continuous service during any incident.
